About cross-site scripting (XSS) attacks
Cross-site scripting is the injection of client-side scripts into web applications, which is enabled by a lack of validating and correctly encoding user input. Learn here, how you can efficiently fix XSS vulnerabilities.
Security assessment
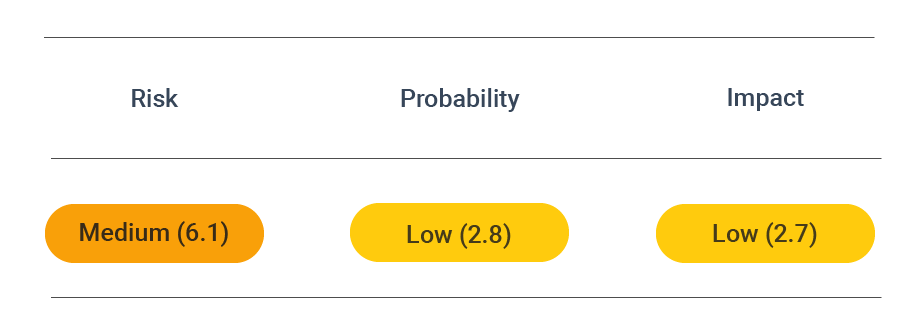
CVSS vector: AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
Vulnerability information
Cross-site scripting (XSS) is the injection of client-side scripts into web applications, which is enabled by a lack of validating and correctly encoding user input. The malicious scripts are executed within the browser and enable various attacks, from stealing the end-users session to monitoring and altering all actions the end-user performs on the affected website. This is possible whenever user input (for example, on a website) is not sufficiently validated on the client- or the server-side.
This includes altering all user actions on that website since the browser does not know that this script cannot be trusted. Because this script is trusted, it can access, e.g., cookies or session tokens or even alter the content of an HTML Page.

It can be injected persistently or non-persistently, depending on the type of XSS that is being used. Usual vehicles of cross-site scripting attacks include search forms, forums, or comment sections.
Types
There are different types of cross-site scripting attacks introduced in the following sections.
Different types of XSS attacks distinguish if the malicious scripts could be injected non-persistent or persistent. Furthermore, there is a differentiation between the vulnerability caused by a flawed input validation on the client- or server-side.
There three main types of cross-site scripting attacks are:
- Stored XSS
- Reflected XSS
- Dom-based XSS
Stored XSS (persistent)
A Stored Cross-site Scripting vulnerability allows an attacker to inject a malicious script persistently into a web application.
In a Stored XSS example, the script might have been submitted using an input field to the web server, which did not perform a sufficient validation and stored the script persistently in the database. The consequence might be that this script is now being delivered to all users visiting the web application and, e.g., gaining access to the user session cookies.
- The script is persistently stored in the web app
- Users visiting the app after the infection retrieve the script
- Malicious code exploits flaws in the web application
- The script and the attack are visible on the server-side (to the app owner)
Reflected XSS (non-persistent)
A Reflected Cross-site Scripting Vulnerability appears if unvalidated input is directly displayed to the user.
In a Reflected XSS example, the input of a search form is reflected on the page to show what the search key was. An attacker may craft a URL that contains malicious code and spread the URL using e-mail or social media. A user who selects this link opens the (valid) web application, which then runs the malicious code in the browser.
- The script is not stored in the web application
- Malicious code is shown to only one user
- Users that open the link execute the script when an app is opened
- The script and the attack are not necessarily visible on the server-side (to the app owner)
DOM-based XSS
DOM stands for Document Object Model and is an interface to web pages. It is an API to the page, allowing programs to read and manipulate its content, structure, and styles.
A DOM-based XSS attack may be successfully executed even when the server does not embed any malicious code into the webpage by using a flaw in the JavaScript executed in the web browser. For example, malicious code can be executed if the client site JavaScript modifies the DOM tree of the webpage based on an input field or GET parameter without validating the input.
- The script is not stored in the web application
- Malicious code is shown to only one user
- Malicious code exploits flaws in the browser on the user side
- The script and the attack are not necessarily visible on the server-side (to the app owner)
Prevent attacks
To prevent XSS attacks, treat all user input as potentially malicious and follow some programming guidelines:
Avoid untrusted input
XSS attacks only appear if any user input is displayed on the webpage. Therefore, try to avoid revealing any (untrusted) user input, if possible. If you need to display user data, restrict the places where the user input might appear. Any input displayed inside a JavaScript tag or a URL shown on the site is much more likely to be exploited than the input that appears inside a div or span element inside the HTML body.
Filter user input
When untrusted input is shown as normal text inside an HTML tag, filter out the characters that allow an attacker to insert a <script> tag on the page. Use the following functions for that:
htmlspecialchars($input) # PHP
html.escape(input, quote=True) # Python
org.apache.commons.lang.StringEscapeUtils.escapeHtml(input) # Java
In JavaScript, you need to define an extra function for this task. You may use:
function escapeHtml(text) {
var map = {
'&': '&',
'<': '<',
'>': '>',
'"': '"',
"'": '''
};
return text.replace(/[&<>"']/g, function(m) { return map[m]; });
}
When user input needs to be inserted into tag attributes or inside a script, you will need to use more robust escape mechanisms. See the XSS Prevention Cheat Sheet for more information. This is the case if you plan to allow user input in cases such as:
<a href="http://example.org/search/q?...USER INPUT..."></div>
<script>alert('...USER INPUT...')</script>
<style> { property: ...USER INPUT...; } </style>
Fix DOM-based XSS
To prevent a DOM-based XSS attack, you could use a save JavaScript property like element.text content for untrusted user input. This prevents the browser from rendering the potential JavaScript code inside the untrustedVariable. So, for example, one of the Dom XSS examples could look like the following code snippet:
element.textContent = untrustedVariable
Furthermore, it is essential to use secure JavaScript functions like inner text or text content instead of innerHtml. Finally, it is always good to remember that it is perilous to pass user-controlled inputs into your web application without proper sanitization.
For further information, OWASP provides a specific DOM-based XSS Prevention Cheat Sheet, including an additional set of rules for securing your web application from DOM-based XSS.
Use an XSS vulnerability tool
As mentioned earlier, XSS attacks are sometimes difficult to detect. However, this can be changed if you get some external help. Another way to prevent XSS Attacks is using the XSS Tool. Still, manual testing is highly time-consuming and costly and, therefore, not possible to be done for every iteration of your web application.
Consequently, your code should not be untested before any release.
Using automated security, you can scan your web application for Cross-Site Scripting and other critical vulnerabilities before every release you do. This way, you can ensure that the Live-Version for your web application is still secured whenever you alter or add a feature.
Enable a Content Security Policy (CSP)
This can prevent not just Cross-Site Scripting attacks but also Cross-Site Injection attacks.
For more information, see XSS Page.