Disable deprecated SSL protocol versions
An SSL/TLS version from the server is outdated. The deprecated versions contain weak implementations that cannot be considered secure anymore. Ensure that your web server provides only recent and substantial protocol versions.
The terms "SSL," "SSL/TLS," and "TLS" are frequently used interchangeably, and in many cases, "SSL" is used when referring to the more modern TLS protocol.
Security assessment
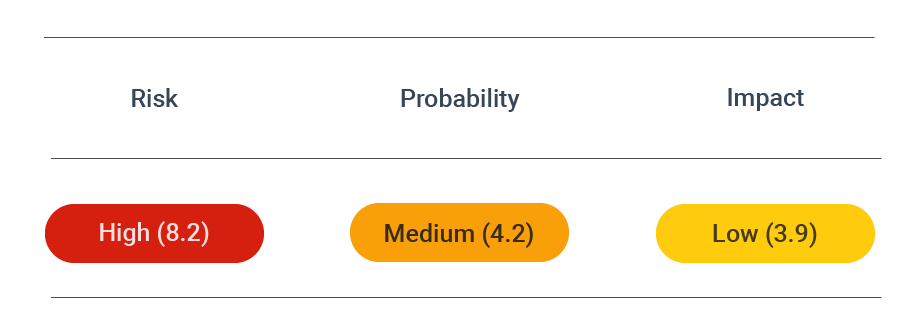 CVSS vector: AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N
CVSS vector: AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:N
Vulnerability information
An SSL/TLS version offered by the server is outdated. The deprecated versions contain weak implementations that cannot be considered secure anymore. Ensure that your web server only offers recent and robust protocol versions.
In their latest cheat sheet for Transport Layer Security (TLS), the OWASP guide recommends the following settings:
- The SSL protocols have many weaknesses and should not be used in any circumstances.
- General-purpose web applications should only support TLS 1.2 and TLS 1.3, with all other protocols disabled.
SSL versions 2 and 3
Secure Socket Layer (SSL) was the original protocol used to provide encryption for HTTP traffic in the form of HTTPS. There were two publicly released versions of SSL - versions 2 and 3. Unfortunately, both have severe cryptographic weaknesses and should no longer be used.
TLS version 1.0 to 1.3 (SSL version 3.1 to 3.4)
For various reasons, the next version of the protocol (effectively SSL 3.1) was named Transport Layer Security (TLS) version 1.0. Subsequently, TLS versions 1.1, 1.2, and 1.3 have been released.
Prevent attacks
To disable the deprecated SSL/TLS protocol versions, see Secure TLS configuration.