Disable RC4
The server supports RC4 (Rivest Cipher 4), a cipher stream that is considered insecure due to multiple known vulnerabilities.
Security Assessment
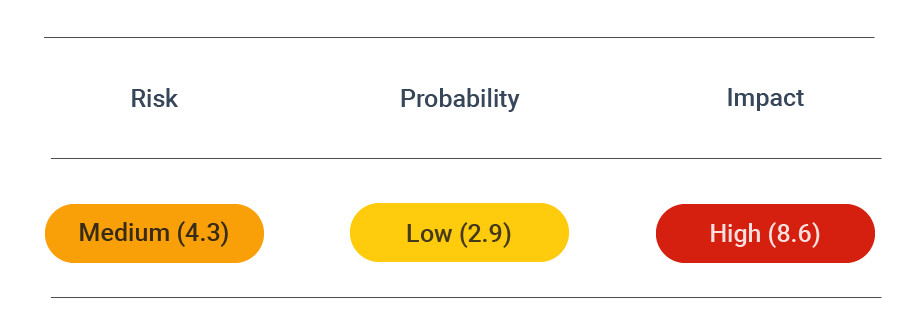 CVSS vector: AV:N/AC:M/AU:N/C:P/I:N/A:N
CVSS vector: AV:N/AC:M/AU:N/C:P/I:N/A:N
About RC4 encryption
The server supports RC4 (Rivest Cipher 4), a considered cipher stream.
RC4 is an abbreviation of Rivest Cipher 4. It is sometimes referred to as ARC4 or ARCFOUR as well. Combined with a plaintext file, it can be used for encryption with the Exclusive Or (X-OR) operation.
RC4 is a stream cipher created by Ron Rivest for the network security company RSA Security back in 1987. That is why it has also become known as Ron's Code.
Stream ciphers work byte-by-byte on a data stream. RC4, in particular, is a variable key-size stream cipher using 64-bit and 128-bit sizes. The cipher uses a permutation and two 8-bit index pointers to generate the keystream. The permutation is done with the Key Scheduling Algorithm (KSA) and then is entered into a Pseudorandom Generation Algorithm (PRG), which generates a bitstream.
The pseudorandom stream that the RC4 generates is as long as the plaintext stream. Then through the Exclusive Or (X-OR) operation, the stream and the plaintext create the ciphertext. Unlike stream ciphers, block ciphers separate plaintext into different blocks. Then it attaches the plaintext to the blocks and performs encryption on them.
What does the encryption procedure look like for RC4? First, the user enters a plaintext file and an encryption key. Then, the RC4 encryption engine generates keystream bytes with the help of the Key Scheduling Algorithm and the Pseudo-Random Generation Algorithm. Finally, the X-OR operation is executed byte-by-byte, and the byte output is the encrypted text, which the receiver gets. They can access the plaintext stream once they decrypt it through a byte-by-byte X-OR process.
RC4 vulnerability and attacks
Despite the advantages of RC4, numerous vulnerabilities have been identified. As a result, it is now considered insecure as a form of encryption and is more and more rarely used.
For example, since RC4 does not require authentication, a Manipulator-in-the-Middle attack (MITM) can be executed. Also, since RC4 is a stream cipher and not a block cipher, it is more vulnerable to a bit-flipping attack. Finally, RC4 has also been found to be susceptible to plaintext recovery attacks and several other security risks.
Here are the most prominent RC4 issues and attacks identified over the years:
- Roos biases: there are a keystream-key correlation and permutations-key correlations, as well as other types of biases.
- Biased outputs: RC4 produces keystreams that can be biased to different extents, which makes them vulnerable to distinguishing attacks.
- Fluhrer Mantin Shamir attack: the first bytes of RC4 keystreams are not random and thus expose information about the key, which opens the doors for WEP attacks.
- Andreas Klein attack: like in previous attacks, even more correlations between the key and the RC4 keystream were discovered.
- Combinatorial problems: problems with the number of inputs and outputs were discovered.
- Royal Holloway attack: security researchers at the Information Security Group at Royal Holloway, University of London identified breaches and attack scenarios that can affect TLS and SSL protocols and WPA/TKIP implementations.
- Bar-mitzvah attack: RC4 ciphers can be used to attack SSL protocols.
- Numerous Occurrence MOnitoring & Recovery Exploit (NOMORE) attack: vulnerabilities for both TLS protocols and WPA/TKIP were discovered, including the Fluhrer-McGrew biases.
Whether you are still using RC4 or not, you can use the DAST Essentials SSL/TLS Scanner to identify and stop potential cyber threats to your systems.
Prevent attacks
Choose only cipher suites with robust encryption algorithms. See secure TLS configuration.