Enable secure cookies
You can transfer cookies that are not marked as secure over an unencrypted connection. A man-in-the-middle attack can be used to get the contents of these cookies.
Security assessment
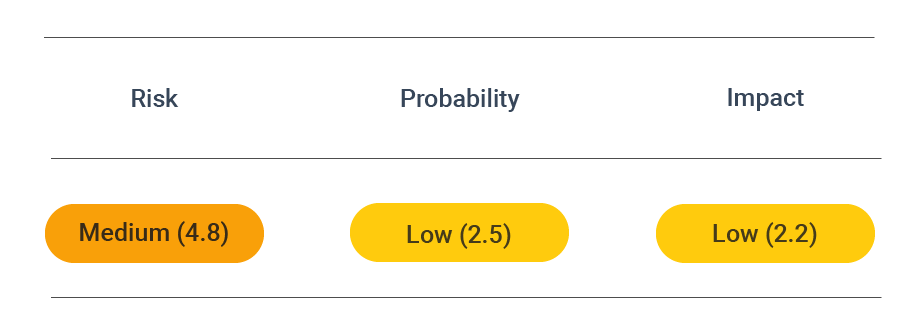
CVSS vector: AV:N/AC:H/PR:N/UI:N/S:U/C:L/I:L/A:N
Vulnerability information
Cookies that are not marked as secure can be transferred over an unencrypted connection. A man-in-the-middle attack can be used to get the contents of these cookies.
Local scripts can read cookies that are not marked as HTTP-only. In the case of a Cross-Site-Scripting (XSS) attack, an attacker can read these cookies.
Think of enabling both settings for all cookies depending on the cookie content. This is especially important for session cookies.
Prevent attacks
To set cookies to secure an HTTP-only, you need to configure the web framework which issues the cookies. Follow these guides for the correct settings:
PHP
In PHP, configure the cookie settings for all delivered websites. Set the following in your /etc/php/php.ini file:
session.cookie_secure = 1
session.cookie_httponly = 1
Django
In Django, make the following cookie settings in your project configuration file:
SESSION_COOKIE_HTTPONLY=true
SESSION_COOKIE_SECURE=true