Prevent fingerprinting attacks
How to prevent web application framework information leakage
Obtaining information about the used web application frameworks is crucial for any attacker. In addition, some vulnerabilities in specific frameworks may give an attacker the needed attack vector.
Security assessment
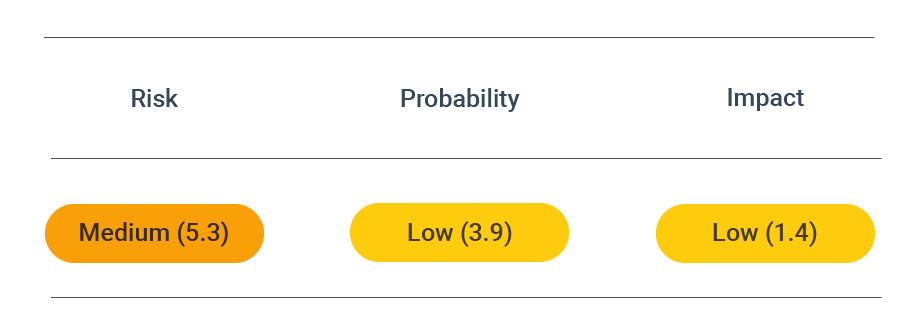
CVSS vector: AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N
Vulnerability information
Obtaining information about the used web application frameworks is crucial for any attacker. Some vulnerabilities in specific frameworks may give an attacker the needed attack vector. To complicate the information gathering process for attackers, the web application should not provide information about used frameworks, especially their versions.
For simplicity, DAST Essentials does not differentiate between used framework languages such as PHP, content management systems such as WordPress, or frameworks such as JQuery.
This scanner addresses the OWASP Top 10 vulnerability of "Using components with known vulnerabilities." While it is crucial to ensure you use the latest version of your web application frameworks, it is an added layer of security if you can prevent attackers from knowing which web application framework and version you are running.
Prevent attacks
Use the following guides to check possible sources of web application framework information leakage and remove the information from the delivered websites:
- PHP
- WordPress - powered by
- WordPress - Meta Generator
- General Hints
PHP
PHP advertises its version based on a setting in its configuration file. To disable this function, make the following entry in the config file usually located at /etc/php.ini:
expose_php = Off
WordPress
WordPress advertises its presence by several means. You should check each of them.
Powered by
WordPress themes usually add a footer that shows something like "Proudly powered by WordPress."
First, check whether your theme has settings for the footer to remove this notice. If so, you will find them in the menu under Appearances > Themes > Customize. You may see a Footer Area or Copyright Area option there where you can remove the corresponding code.
If your theme does not come with such settings, you need to edit the theme yourself. Go to Appearances > Editor > Theme Footer (footer.php). The code will look something like this:
<?php
/**
* The template for displaying the footer
*
* Contains the closing of the "site-content" div and all content after.
*
* @package WordPress
* @subpackage Twenty_Fifteen
* @since Twenty Fifteen 1.0
*/
?>
</div><!-- .site-content -->
<footer id="colophon" class="site-footer" role="contentinfo">
<div class="site-info">
<?php
/**
* Fires before the Twenty Fifteen footer text for footer customization.
*
* @since Twenty Fifteen 1.0
*/
do_action( 'twentyfifteen_credits' );
?>
<a href="<?php echo esc_url( __( 'https://wordpress.org/', 'twentyfifteen' ) ); ?>"><?php printf( __( 'Proudly powered by %s', 'twentyfifteen' ), 'WordPress' ); ?></a>
</div><!-- .site-info -->
</footer><!-- .site-footer -->
</div><!-- .site -->
<?php wp_footer(); ?>
</body>
</html>
Remove all information there that will leak your used system. A sanitized version might look something like this:
<?php
/**
* The template for displaying the footer
*
* Contains the closing of the "site-content" div and all content after.
*
* @package WordPress
* @subpackage Twenty_Fifteen
* @since Twenty Fifteen 1.0
*/
?>
</div><!-- .site-content -->
<footer id="colophon" class="site-footer" role="contentinfo">
<div class="site-info">
Your footer Notice
</div><!-- .site-info -->
</footer><!-- .site-footer -->
</div><!-- .site -->
<?php wp_footer(); ?>
</body>
</html>
Meta Generator
WordPress inserts a meta generator tag into your website code. It shows up in the HTML source code as:
<meta name="generator" content="WordPress 4.7.4" />
It would be best if you disabled the meta generator by adding a function to your theme settings. Open Appearances > Editor > Theme Functions (functions.php). Then, add the following code:
/**
* Remove meta generator link
*/
remove_action('wp_head', 'wp_generator');
General hints
Search in your web application for the following keywords:
- X-Powered-By
- PoweredBy
- MetaGenerator
- Version
Leaked version information will often be nearby those keywords. If you have isolated which framework leaks its version, you can look for a specific solution.
Prevent webserver information leakage
Obtaining information about the used web server is crucial for any attacker. There may be vulnerabilities in a particular web server version that allow an attacker easy access to the server.
Security assessment
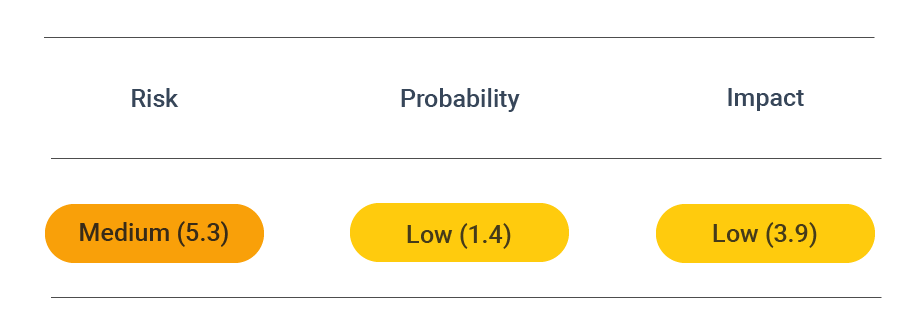
CVSS vector: AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N
Vulnerability information
Obtaining information about the used web server is crucial for any attacker. There may be vulnerabilities in a particular web server version that allow an attacker easy access to the server. To complicate the information gathering process for attackers, the webserver should not provide information about itself, such as its name or version.
This scanner addresses the OWASP Top 10 vulnerability of "Using components with known vulnerabilities." While making sure you use the latest version of your webserver is crucial, it is an added layer of security to prevent attackers from knowing which webserver - and which version you are running.
Prevent attacks
Use one of the following guides to disable information leakage for your webserver:
- Apache
- Apache 2.2
- nginx
- IIS
Apache
To disable the server signature, which usually contains the name and version for an Apache web server, do the following:
Open the Apache configuration file on your system. This file is usually located at:
/etc/apache2/apache2.conf(Debian, Mint, Ubuntu)/etc/httpd/conf/httpd.conf(Arch, Fedora, CentOS, RHEL)
Depending on the server configuration, there might also be additional configuration files that take care of security configuration such as /etc/apache2/conf-enabled/security.conf.
Apply the following settings:
Then reload the web server configuration:
Apache 2.2
In addition to the server signature, Apache version 2.2 has another feature that can leak its version. A header image for the standard installation contains the version information. The problematic images are usually located in/usr/share/apache2/icons/. They are linked to being publicly available as icons by an alias configuration. To stop them from being delivered, edit the configuration file/etc/apache2/mods-available/alias.confand remove the following lines:
-a0f1496a0bafdbf530eddf370a68c2f7.png) https://github.com/crashtest-security/gist/blob/master/fingerprinting/apache2.2_settings
https://github.com/crashtest-security/gist/blob/master/fingerprinting/apache2.2_settings
Nginx
To disable the version string, which is usually sent by Nginx, update the configuration file, which is generally located at /etc/nginx/nginx.conf, and add to the HTML section:
To disable that the server name is sent, you need the HttpHeadersMoreModule. Run the following commands for installation:
apt-get install nginx-extras # Debian, Ubuntu
yum install nginx-extras # Fedora
yaourt -S nginx-mod-headers-more-git # Arch with yaourt package manager to install aur packages
For other systems (such as CentOS or RHEL), you need to compile the package from the sources as described in the installation notes.
Then also, add the following line to the config file within the HTML section and choose a server name of your liking:
Limiting Information Provided by IIS
The IIS server also exposes its version in HTTP responses. Microsoft provides UrlScan, which you can use to remove server information from HTTP responses sent by IIS. UrlScan requires IIS6 Metabase compatibility. Additionally, the configuration made to IIS is global. If you would like to set up this configuration on a site-by-site basis, see the UrlScan Setup article from Microsoft.
- Enable Metabase Compatibility. For instructions, see the Microsoft documentation.
- Install UrlScan.
- Open the
UrlScan.inifile in a text editor. The file is typically located in the directory%windir%\system32\inetsrv\UrlScan. - Search for the key
RemoveServerHeader, which by default is set to0. Set the worth to1to remove theServerheader.

-87d8a65a678137c22964cbf13bf98637.png)
-143d9894178f07f564506097af9ba8ba.png)