Prevent Heartbleed attacks
The Heartbleed bug allows attackers to steal the private key of a server certificate. If the server is vulnerable to Heartbleed, an attacker can retrieve the private key and impersonate the server.
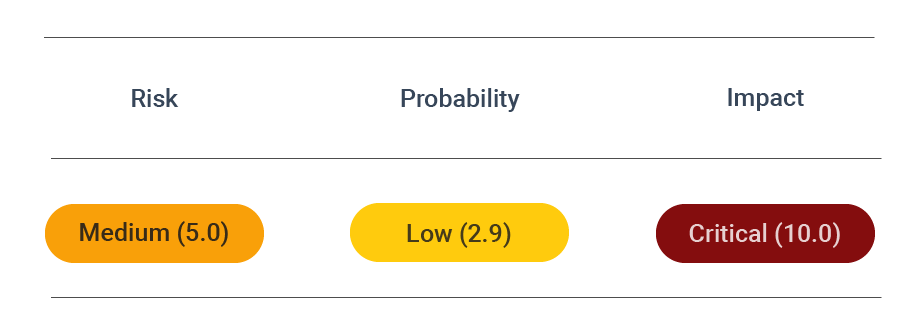
Security Assessment
CVSS vector: AV:N/AC:L/AU:N/C:P/I:N/A:N
Vulnerability information
The Heartbleed bug is classified within the Common Vulnerabilities and Exposures of the Standard for Information Security Vulnerability Names maintained by MITRE asCVE-2014-0160. It is a buffer over-read a case when a system allows data access that should be restricted.
What is the Heartbleed vulnerability in a nutshell? It allows attackers to steal the private key of a server certificate. If the server version is vulnerable to Heartbleed, cybercriminals can retrieve the private key and impersonate the server. The consequences can be quite dire, as secure connections to the server are not possible anymore, and private information can be easily exposed.
Affect of the Hearbleed bug your web application
The impact of the Heartbleed bug has been widespread and is thus considered critical. The consumer sites using OpenSSL display a 'lock' icon next to the address and an s in the web address (at the end of 'https'). It signifies that the website encrypts and protects private data.
As of April 2014, the open-source web servers Apache and Nginx, which use OpenSSL, made up two-thirds of all active sites' online market share. This gives an idea of the massive scope of the Heartbleed vulnerability. It affected digital companies and public bodies like the Canada Revenue Agency.
Since attacks leave no traces in the logs, intrusion detection and estimation of the actual exploitation attempts and successes of the Heartbleed bug are difficult. Furthermore, users can take specific protective actions since the problem was with vulnerable servers. First, however, users needed to install updates and change passwords to ensure their credentials wouldn't be stolen whenever the bug was fixed in a system.
Prevent attacks
Update OpenSSL to the latest version. The following versions are known to have fixed the Heartbleed vulnerability:
- OpenSSL 1.0.1g
- OpenSSL 1.0.0 (not affected)
- OpenSSL 0.9.8 (not affected)
E.g., run:
apt-get update; apt-get upgrade # Debian / Ubuntu
yum update # RHeL / CentOS
pacman -Syu # Arch Linux
This step is critical because the risk of attacks remains if you're running vulnerable versions of OpenSSL.