Renew TLS certificates
The domain certificate is expired or will expire closely. An expired certificate will result in user error messages for the web application.
Security assessment
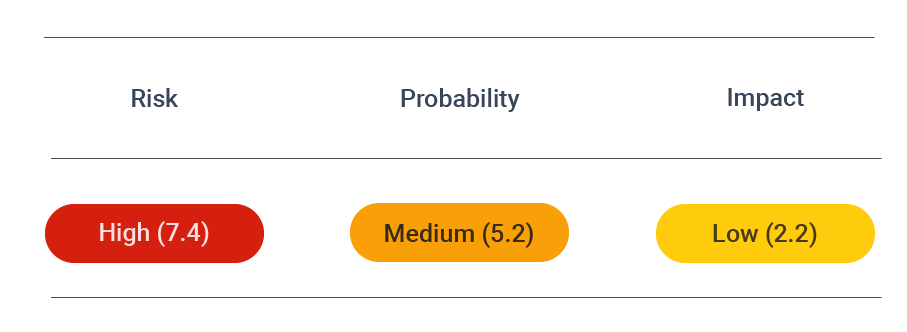
CVSS vector: AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:N
Vulnerability information
The domain certificate is expired or will expire very closely. An expired certificate will result in user error messages for the web application. To guarantee secure connections between the users and the web server, request a newly signed certificate with your certificate authority.
Prevent attacks
Use one of the following options to renew your certificates.
OpenSSL
To generate a certificate signing request for your certificate, run:
openssl req -new -key ssl/certificate.key -out ssl/certificate_signing_request.csr
This assumes that your certificate to renew (including private key) is stored in ssl/certificate.key. Then submit the certificate_signing_request.csr to your certificate authority. They will use this request to sign your certificate and provide you with the signed certificate if the signed certificate is returned to you as new.crt, you can combine the key and the signed certificate as follows:
cp ssl/certificate.key ssl/new.pem
cat ssl/new.crt >> ssl/new.pem
The resulting new.pemfile can be copied to your webserver directory to be used in the web application.
Let's Encrypt
If you are using Let's Encrypt as your certificate authority, run the certbot renew command:
certbot renew
To enable manual renewal, add the renew command to your crontab by running Sudo crontab -e:
# m h dom mon dow command
0 0 * * 0 certbot renew
This will run the renew command once a week at midnight trying to restore all your certificates.